Cloud computing has revolutionized today’s digital landscape, transforming how businesses operate and manage their data. The COVID-19 pandemic accelerated this shift, pushing enterprises to migrate workloads to the cloud to enhance efficiency and streamline processes. According to the Flexera 2021 State of the Cloud Report, an impressive 90% of businesses anticipate continued growth in cloud adoption. However, as companies rush to leverage this powerful tool, it is crucial to pause and consider the numerous risks associated with cloud usage. To safeguard their data and maintain operational integrity, enterprises must be vigilant about these threats as they embrace this new paradigm.
Cloud computing exists in various forms, catering to the diverse needs of organizations. These forms range from the private cloud, dedicated to a single user, to public clouds accessible to multiple users. Additionally, hybrid and multi-cloud strategies allow organizations to combine different cloud environments, tailoring their approach to meet specific operational demands. No single cloud type can be deemed superior; rather, the best choice hinges on the unique requirements of each organization.
The applications of cloud computing are extensive and diverse. For example, popular services like Dropbox and Gmail demonstrate how files can be stored in the cloud, liberating users from the limitations of physical devices. In industries such as finance and healthcare, cloud computing is essential for securely storing sensitive information, including financial records and patient data. Additionally, advancements like telemedicine have harnessed cloud capabilities, enabling seamless diagnostics and patient care across multiple facilities. Even government agencies have adopted cloud computing to streamline operations, such as issuing court summons, showcasing its widespread use across various sectors.

Concerns about cloud security
Despite the advantages, concerns about cloud security persist. Many of the security threats that plague traditional data centers parallel those faced in cloud environments. Cybercriminals exploit vulnerabilities in software, and as organizations migrate to the cloud, they must navigate the complexities of shared responsibility between the cloud service provider (CSP) and their internal IT teams. This relationship necessitates a thorough understanding of both parties’ roles in maintaining cloud security, as lapses can have dire consequences.
As organizations ponder the shift to cloud computing, they must remain vigilant about the security risks inherent in this transition. Some of the most pressing concerns include limited visibility into network operations, malware threats, compliance challenges, data leakage, inadequate due diligence, data breaches, and poor application programming interfaces (API). Each of these risks presents a unique challenge, requiring organizations to adopt comprehensive strategies to mitigate potential vulnerabilities.

Firstly, the loss of visibility into network operations is a significant concern when organizations entrust their workloads to CSPs. As the responsibility for certain systems and policies shifts to the provider, organizations must develop alternative monitoring solutions to maintain oversight of their network infrastructure. Without effective network-based monitoring and logging, identifying potential security threats becomes increasingly challenging.

Malware poses another substantial risk in cloud environments. By storing substantial volumes of sensitive data in internet-connected clouds, organizations expose themselves to heightened vulnerabilities. Studies indicate that nearly 90% of organizations are more likely to experience data breaches as their cloud usage grows. The evolving tactics employed by cybercriminals necessitate constant vigilance and proactive measures to thwart potential attacks.
Compliance is an increasingly significant challenge, with stringent regulations like GDPR, HIPAA, and PCI DSS imposing greater demands on organizations to protect data privacy. A vital aspect of compliance is monitoring user access to ensure that only authorized personnel can access sensitive information. Given that cloud systems often support large-scale user access, implementing robust access controls is crucial for maintaining compliance and safeguarding data.
Data leakage remains a pressing concern, with over 60% of organizations citing it as their top cloud security worry. This risk arises from the need to relinquish some control to the CSP, which means that the security of vital data may depend on an external entity. In the event of a breach at the CSP level, organizations not only risk losing invaluable data but may also face liability for damages incurred due to the incident.
Moreover, inadequate due diligence can impede a successful transition to the cloud. Organizations must thoroughly evaluate the scope of work required for effective migration, ensuring they comprehend their CSP’s security measures. Neglecting proper due diligence can result in unforeseen vulnerabilities and security gaps during the transition process.
One of the most concerning risks in cloud computing is the potential for data breaches. Inadequate security measures can allow malicious actors to access sensitive data stored on cloud servers, leading to severe financial and reputational damage for organizations. A single breach can cost millions and tarnish an organization’s reputation, underscoring the need for a robust security approach.
Additionally, poorly designed APIs can expose cloud resources to unnecessary risks. Cybercriminals may exploit weak APIs through various methods, such as brute force attacks and denial-of-service attacks, compromising the integrity of the cloud environment.
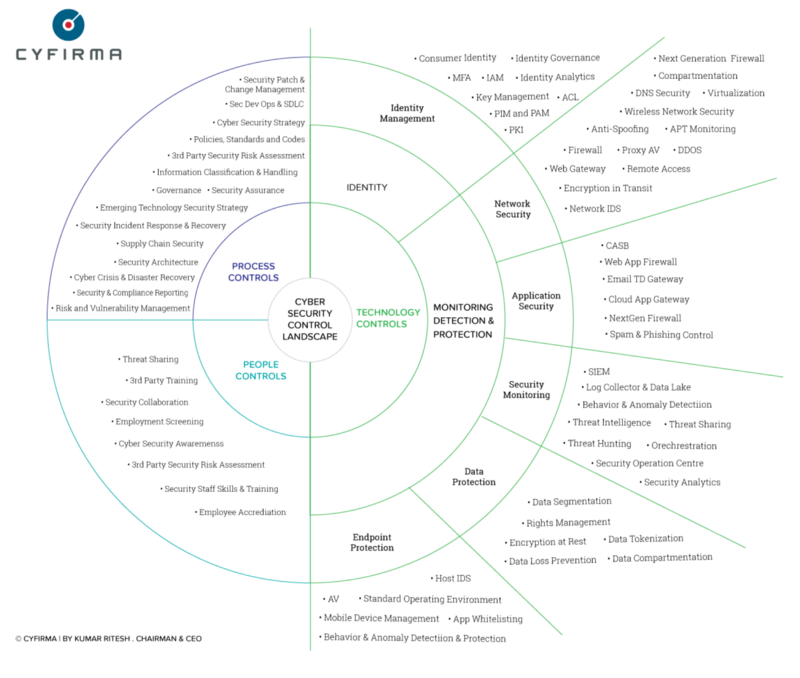
Measures we need to take
In light of these security threats, organizations must proactively bolster their cloud security measures. Risk assessments are crucial in evaluating an organization’s cybersecurity posture and identifying potential vulnerabilities. By conducting thorough evaluations, IT teams can make informed decisions to enhance security protocols moving forward.
Implementing user access controls is another vital strategy for ensuring cloud security. Organizations should consider adopting a zero-trust security model, which operates on the principle that no user should automatically be trusted with unrestricted network access. By granting users access only to the critical functions necessary for their roles, organizations can mitigate the risk of unauthorized access to sensitive data.
Automation can also significantly improve cloud security by streamlining repetitive processes and allowing IT teams to focus on high-priority tasks. By automating key initiatives such as cybersecurity monitoring and threat intelligence collection, organizations can enhance their response to emerging threats and reduce the burden on their IT departments.
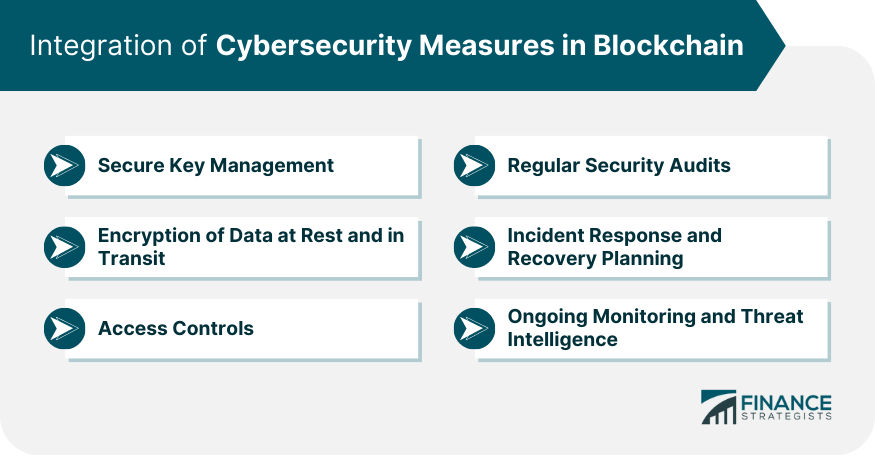
Continuous monitoring is perhaps the most critical aspect of a successful cybersecurity risk management program in the cloud. As the digital landscape evolves, organizations must rely on ongoing assessments to maintain proper cyber hygiene. Point-in-time evaluations may no longer suffice; continuous monitoring allows organizations to respond swiftly to potential security threats before they escalate into significant issues.
Finally, employee security training cannot be overlooked. Organizations should prioritize educating employees about cloud computing risks and best practices for safeguarding sensitive data. Many cloud storage providers offer training resources, ensuring that employees understand how the cloud operates and the necessary controls to enhance security efforts.
As businesses increasingly adopt cloud computing, the interplay between innovation and security threats becomes more evident. By understanding the potential risks and implementing strong security protocols, enterprises can navigate the complexities of cloud computing, reaping its benefits while protecting their critical information. The future of cloud computing is promising, but achieving it will require preparation, effort, and a commitment to security.
Related posts:
Top 7 Security Risks of Cloud Computing
What is Cloud security?
Cloud Computing: Big Opportunities and Big Threats